Cybersecurity for Case Managers: Don’t Get Hooked - "How to Prevent Being Caught in a "Phishing" Attack
 Print this Article | Send to Colleague Print this Article | Send to Colleague
Pat Stricker, RN, MEd
Senior Vice President
TCS Healthcare Technologies
This is the
third article in a series on cybersecurity related to the healthcare industry.
The first two articles dealt with the incidence
and impact of cybersecurity breaches and the responsibilities
of each individual case manager in preventing breaches. This article will
discuss the incidence and significance of "Phishing" and what you can do to
make sure you are not caught in a phishing attack.
Phishing is
a scam aimed at getting an online user to reveal personal or confidential
information for the purpose of identity theft. There are three types
of attacks:
- Phishing is an exploratory
attack targeted at a broad audience to manipulate victims into opening file
attachments or embedded links in an email. The scammers goals are to obtain
sensitive data, personal information or user/network credentials that can lead
them deeper into an organizations data. A basic attack is distributed en masse
or blasted out like spam.
- Spear phishing is a targeted phishing
that is more sophisticated and elaborate than a phishing attack. It focuses on a
specific company or individual and combines tactics like personalizing or
impersonating users so the spear phishing email is extremely accurate and
compelling. It also attempts to bypass or evade email filters and antivirus
software. The goals are the same - to coerce a target into opening an
attachment or embedded link that provides long-term access into an
organizations system and the ability to introduce malware, Trojans, key
loggers, port listeners and multi-vector attacks.
- Whaling is very similar
to spear phishing, but a more specific form of attack, targeting corporate
upper management by name with the intent of obtaining confidential company
information. Whaling involves using an email or webpage that appears legitimate
and contains a high sense of urgency. It is often disguised as a legal
subpoena, client complaint or internal executive directive.
A phishing
scam typically starts with a legitimate-appearing email from a person, company or website asking the user to update personal information, such as a password,
credit card, social security number or bank account number. The message looks
authentic and comes from organizations a user may have accounts with. It also
may include legitimate-looking company logos and formats that the company uses.
In fact, it usually looks so authentic that up to 20 percent of recipients
respond to them and 91 percent of data
breaches start with a phishing attack. The average cost
of a phishing attack is $1.8 million. In fact, the 2015 HIMSS
Cybersecurity Survey of 300 top health care information
professionals stated that phishing attacks are their biggest future security
fear and the #1 thing
that keeps Chief Information Security Officers up at night.
The Phishing
Activity Trends Report shows that there were 630,404 unique
phishing attacks detected from January to September, 2015. This means 36 percent of
the world;s computers are infected with this type of malware. While some
employees are specifically targeted because of their position or types of
information they have access to, all individuals and companies should assume
they are or will be targets of phishing attacks.
Phishing
scams are frequently presented in the form of spam or pop-ups that are
introduced through email. To make sure you are not a victim of a phishing attack,
let's review some things you can do to prevent getting "hooked." Two
articles, 8 Ways to
Prevent "Phishing Scams" and 10 Tips to
Prevent Phishing Attacks provide the following useful suggestions to
help guard against phishing:
- Learn to identify phishing
emails, such
as those that:
o Are not personalized.
o
Come from unknown senders.
o
Ask you to confirm/update
personal information (especially when they are urgent).
o
Threaten you with
frightening information, if you do not respond.
o
Duplicate
the image of a real company or are visually similar to a real business.
o
Copy the
name of a company or an actual employee of the company.
o
Promote
gifts, or the loss of an existing account.
- Communicate personal information only via phone or secure websites:
o Do not give personal information over
the phone to anyone who calls you and do not call the phone number provided in
an email asking you to update your information. Look up the number of the
company or organization and call them to verify if the email or call is
legitimate.
o
For email transactions, make sure the website is secure before
giving any information.
- Look for "https" in
the address bar. The "s" means it is secure.
- Look for a padlock in the browser address and a "green address bar",
indicating the site has applied for a SSL
certificate , showing they are the legitimate owner of the website and that information
to and from the site is encrypted.
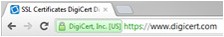 Sites with the new, more protected TLS certificate are safer than those with the older SSL
certificate, since they are protected from eavesdroppers. Sites with the new, more protected TLS certificate are safer than those with the older SSL
certificate, since they are protected from eavesdroppers.
- Even
if the browser address has a padlock or a green address bar, you cannot be guaranteed
that it is totally safe, since "phishers"
are applying for certificates in names of companies that are very similar
to the real website name, e.g. "emergencypaypal.net" or "phypal.com" instead of
"paypal.com" or "banskfamerica.com" instead of "bankofamerica.com".
- If the "phisher" has been able to get a
certificate, the site may have a padlock or a green address bar, but the name
will be a little different than the official site. So check the website name carefully.
- If you are still unsure
about the sites validity, double-click the padlock icon to see the security
certificate. In the "Issued To" in
the pop-up window you will see the name matching the site you think you're on.
If the name differs, you are probably on a spoofed site.
- If your browser gives you a
message about an untrusted security certificate for a website, do not proceed to the website, as
it is not trustworthy.
- Do not download
files or open attachments in emails from unknown senders. Even if emails are from known
senders, be certain you know the files or attachments are trustworthy
before downloading or opening them.
- Files or attachments that you are not expecting could
contain malware that
could infect your computer by downloading unwanted files onto your
system.
- Be wary of links that offer low cost products. They could lead to phishing webpages that can gain access to your credit
card information.
- Beware of embedded
links in emails that ask
you to update your personal information or password, even if the email appears to come from someone you do
business with. Phishing websites, in addition to looking legitimate by
using company logos, links to the site, etc., also try to appear to be a security-conscious organization by notifying you that
your account was compromised and asking you to be proactive and re-register
or change your password. They may even provide a hyperlink to make it "quick
and convenient" for you to update your information. However when you click
on the link, it will take you to the phishing website, not the legitimate
website, and steal your information. To prevent being "caught":
o Hover over the hyperlink to determine the
address of the hyperlink. You should be able to tell if it is the official
website address or a copy-cat. Example: www.banskfamerica.com instead of www.bankofamerica.com.
o Always enter the company website address
yourself or look up the company phone number and call to see if they are requesting
the information. Legitimate businesses usually do not request personal information by email.
o Never enter personal information through
links provided in an email. Only login and enter personal information
once you are sure you are on the official site.
- Beware of pop-ups and follow these tips:
o
Never
enter personal information in a pop-up screen.
o
Do not click on links in a
pop-up screen.
o
Do not copy web addresses from
pop-ups into your browser.
o
Do not submit personal
information into pop-up screens, since legitimate organizations do not ask you
to submit information that way.
o
Enable pop-up blockers.
- Use anti-spyware, firewalls, spam filters, and anti-virus
software.
- Update the programs regularly to assure they are able to
block newly identified viruses and spyware.
- Anti-spyware
and firewalls prevent phishing attacks from gathering data from your
computer, such as webpages containing personal information, like credit
cards.
- Spam
filters identify files that could contain spam (unsolicited commercial
email @ UCE). The filters look for spam based on content, false
information in headers, blacklisted files or known spammers, specific senders or
wording in the subject line or body, or unapproved senders.
- Antivirus
software scans every file which comes through the Internet to your
computer to prevent viruses from deleting files or directory information.
- Consider setting up a free virtual private network (VPN) instead of using free, open, unsecured Wi-Fi networks,
which are easy to compromise. The 2015 Consumer Trust Survey found that 43% of the respondents used
these untrustworthy Wi-Fi networks.
- Password protect all your devices. 61% of the survey's respondents tablets were not password protected.
- Many
smartphones are also vulnerable, because the operating systems are not
regularly updated and the phones do not contain strong, up-to-date anti-virus
and malware protection. And unfortunately, they are often not password
protected, because users say it takes longer to access the content. However,
isn't it better to take a little longer when logging in than to allow your
devices to be unsafe and the target of phishing schemes?
- Be sure to use unique, strong passwords
for all your websites. One-third of the respondents said
they only use one or two passwords for all their websites. This is
dangerous. (See hints for developing strong passwords in last month's article).
- Keep your operating system
and browser updated to the latest version, which addresses the
most current online risks.
- Whenever possible, do not
allow websites to keep your payment information on file.
- Do not share too much
information on social media, such as birthdays, anniversaries,
children's names, what you like, what you are doing at work, etc. All of this can be used to
create very targeted and believable phishing attacks.
- Do not connect and share information with
people you don't really know.
- Do not use your own personal
email while at work or while on your organization's network. Your Internet Service Provider and computer system may not be as
well protected as that of your organization and could be more easily
compromised.
- Do not click on ads, as they may contain malware or direct you to a phishing website.
If you want to learn more about the product, enter the website or product
name in the browser address.
- Go to Anti-Phishing Working
Group for a list of current phishing attacks,
helpful resources and the latest news in the fight to prevent phishing.
- If you think you have been the victim of a phishing attack, be sure
to report it right away to your
organization, so it can be dealt with as soon as possible.
The weakest link in any security system is the human element
and that is particularly true when it comes to phishing attacks. Employees are the biggest threat to phishing attacks, since they are the
ones who initiate the action that allows the phishing scam to occur. In addition, hackers have become more creative in manipulating and
influencing people, which allows them to gain access to computer systems and
obtain sensitive information.
Therefore, most important aspect in
preventing phishing attacks is education. Users must be aware of what to watch
for and vigilant in looking for potential attacks. Regular employee training
can reduce the percentage of successful phishing attacks. In addition to the
regular security training, there are some free phishing tests and tools that
are available to help organizations determine their phishing risk. The spear phishing awareness failure rates,
for the
79 percent of companies who tested their employees, was 16 percent.
To test your employees (or to test yourself), you can use the
following free phishing tools and tests to see
how likely they (or you) are to fall prey to a phishing attack:
- KnowBe4 provides a free phishing security test
for up to 100 employees to determine what percentage of the organization's
users are "phish-prone".
- The Phishing Quiz tests your phishing knowledge to determine how
skilled you are at detecting malicious phishing attempts amid
common work-related emails.
- Phishing Your Employees 101 is a new, simple, open source toolkit
and education program that makes it easy to set up phishing websites and lures
that tests the phishing awareness of employees.
- The Open DNS Phishing Quiz tests employees to see if they can delineate between legitimate and
phishing websites.
Remember, anyone
can be targeted almost anywhere online, so you need to keep an eye out for "phishy"
schemes. I'm sure you don't want to be the one responsible for allowing a
malware, virus, or spyware to gain access to your organizations computer system,
or worse yet, the one responsible for a data breach that resulted from your phishing
attack.
Watch out for the "phish"!
Pat Stricker, RN, MEd, is senior vice president of Clinical Services at TCS Healthcare Technologies. She can be reached at pstricker@tcshealthcare.com.
   
|

 Sites with the new, more protected
Sites with the new, more protected